A new malware is a reminiscent of the statement. It was discovered by Reddit users and according to them; it hibernates in the core folders of your device, and is able to swipe your password and Apple ID.
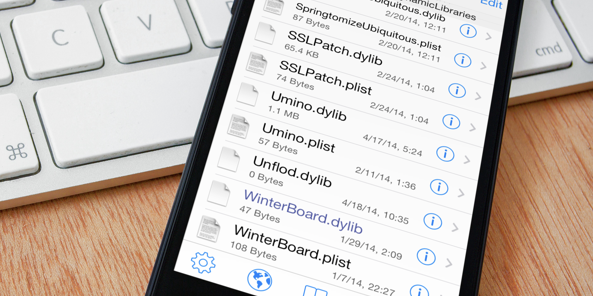
The malware purported ‘Unflod.dylib’ seems to come from China. It’s inside the DynamicLibraries folder; you can browse it through Library/MobileSubstrate/DynamicLibraries/Unflod.dylib. It keeps an eye on outgoing SSL connections, and that’s when it feeds on the Apple ID and password. The information is relayed back to malware creators in plain text.
However, it remains a mystery that how is it able to detect jailbroken devices, which raises further concerns. One theory says that unofficial repositories with unauthorized apps include this malware, but the exact name is unknown.
This is how you can find out if you’re infected:
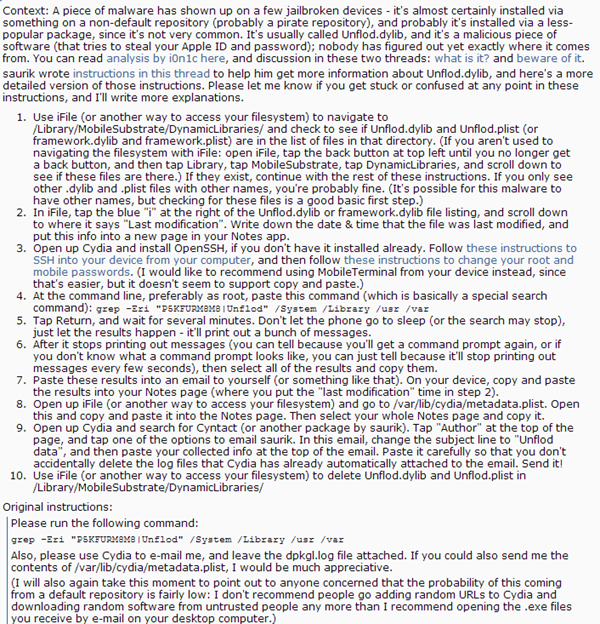
Usually, you should stay away from unrecognisable repositories, and if you’re worried about the issue, you can check the location for the malware as Saurik has instructed on Reddit.
You need to launch iFile or another file browsing application, navigate through /Library/MobileSubstrate/DynamicLibraries. If you find the file Unflod.dylib, chances are you’re infected.
How to remove this malware:
If you do see the malware file, delete it, and remove any tweaks, apps and repos from unrecognizable sources. Another good idea is to change Apple ID, but the best solution is to do a full system restore. This will remove the jailbreak, but keep your personal information safe.
This goes to show that taking apps from questionable resources is always accompanied by risk of malware infection.
You can read the full Reddit post here
You have been warned…