.
Gordon Maddern of Pure Hacking, using a payload derived from the Metasploit framework, was able to send colleagues malicious messages that are able to execute on their remote machines. The Register’s Dan Goodin reports that while Maddern didn’t clarify what specific interactions were needed on the receiver’s end to activate the payload, access to a victim’s machine may potentially give attackers the ability to spread the infection to other machines on the local network, or again via Skype.
Maddern writes,
The long and the short of it is that an attacker needs only to send a victim a message and they can gain remote control of the victims Mac. It is extremely wormable and dangerous.
This news follows a week where Google Images became a vector to spread malware on OS X.
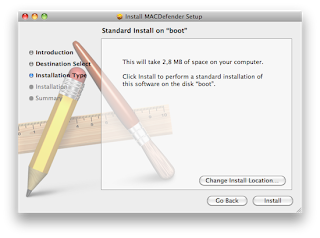
Taking advantage of how Safari handles downloads by default, MacDefender malware (Read Below) has been targeting users browsing Google Images. By scaring recent converts with the possibility that their machines are infected, users are asked to install software to remove the threat. Of course, people still fall for these common methods of attack, and new Mac users may not be fully aware of how their new machines operate.
MacDefender Malware Targets:It is a new malware that quickly spreading among Mac users using the Safari browser to visit certain websites, especially Google Images.
The application, disguised as a virus scanning tool and completely unrelated with the official MacDefender software, gets installed automatically without a user’s consent upon opening a webpage, although it’s not clear what kind of websites allow this kind of installation, and whether MacDefender “phones home†once running on a Mac to download additional pieces of code (like most malwares on Windows do). Some users are reporting they found the app installed on their Macs after visiting webpages linked on Google Images, some say it’s only happening with the Safari desktop browser, others claim the app can’t be removed with a simple drag & drop to the system’s Trash as, once installed, the process will beging running automatically on OS X. Again, it’s not clear what kind of malware MacDefender.app is and the proportion of this “spreading†across Mac OS X machines, but the number of threads on Apple Support Communities seems to suggest at least hundreds of people have experienced the issue in these past few days.
|
Today, Ed Bott from ZDNet detailed what an attack might look like if it happens to you.
Update: This evening, Skype made a statement on their security blog addressing that the issue has already been fixed.
This vulnerability, which they blogged about earlier today, is related to a situation when a malicious contact would send a specifically crafted message that could cause Skype for Mac to crash. Note, this message would have to come from someone already in your Skype Contact List, as Skype’s default privacy settings will not let you receive messages from people that you have not already authorized, hence the term malicious contact.
A hotfix was released in version 5.1.0.922 of Skype for Mac on April 14th. If haven’t yet updated to a more recent version, now would be the time to launch the Skype app and check for an update HERE (Direct Link for Skybe).
{Thanks}
Imp0rtant P0sts Fr0m Redsn0w.us: